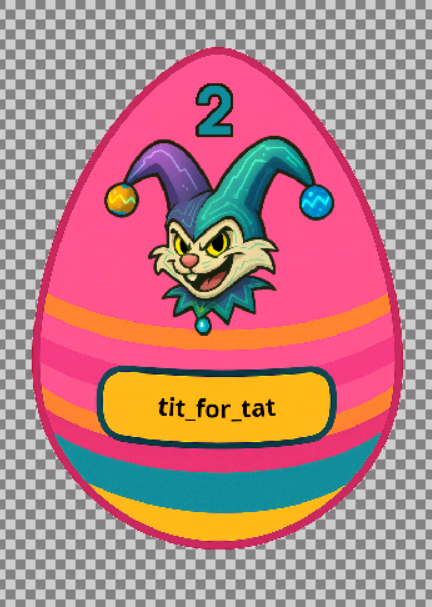Advent of Cyber 2025 - Day 9 - A Cracking Christmas
Day 9 of Advent of Cyber 2025 exploring password cracking techniques using pdfcrack and John the Ripper to crack encrypted PDFs and ZIP files, plus bonus KeePass database cracking for a side quest.
Description
With time between Easter and Christmas being destabilised, the once-quiet systems of The Best Festival Company began showing traces of encrypted data buried deep within their servers. Sir Carrotbane, stumbled upon a series of locked PDF and ZIP files labelled “North Pole Asset List.” Rumours spread that these could contain fragments of Santa’s master gift registry, critical information that could help Malhare control the festive balance between both worlds.
Sir Carrotbane sets out to crack the encryption, learning how weak passwords can expose even the most guarded secrets. Can the Elves adapt fast and prevent their secrets from being discovered?
Learning Objectives:
- How password-based encryption protects files such as PDFs and ZIP archives.
- Why weak passwords make encrypted files vulnerable.
- How attackers use dictionary and brute-force attacks to recover passwords.
- A hands-on exercise: cracking the password of an encrypted file to reveal its contents.
- The importance of using strong, complex passwords to defend against these attacks.
Introduction
This is the ninth challenge in this year’s Advent of Cyber hosted by TryHackMe, a 24 day cyber security challenge where new objectives are released every day. Each objective consists of multiple questions and flags we must find on their machines, sometimes by simply following their instructions and other times by needing to find something hidden ourselves. This challenge focuses on password cracking and encrypted file exploitation. We’ll be investigating how Sir Carrotbane discovered locked PDF and ZIP files labelled “North Pole Asset List” containing fragments of Santa’s master gift registry. Using tools like pdfcrack, john, and fcrackzip, we’ll perform dictionary and brute-force attacks to crack weak passwords protecting these encrypted files. The challenge also explores detection methods for password cracking activities from a blue team perspective. As usual, we begin by launching the target machine and either connecting to it via VPN or using their in browser attack box, which I will be doing.
Solving the Challenge
This challenge takes place on TryHackMe’s machine which you can access via SSH or using their in-browser machine which I will be utilizing.
What is the flag inside the encrypted PDF?
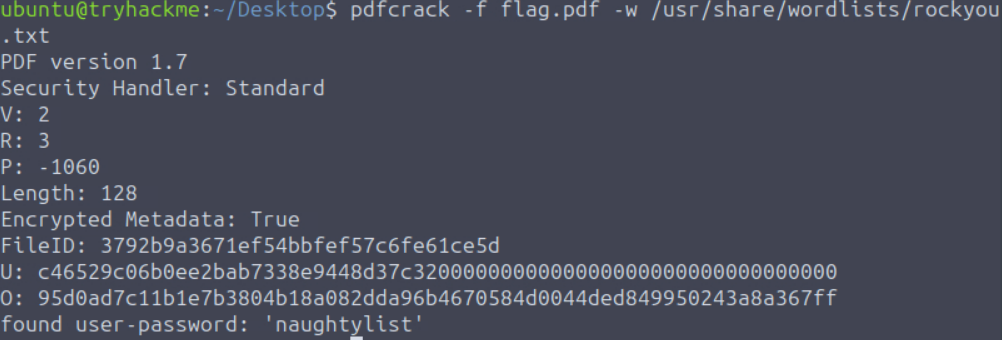
On the desktop we see there is a password protected PDF named flag.pdf. In order to crack PDF passwords we can use the pdfcrack tool which is already installed on the machine. For the wordlist we can use the popular rockyou.txt wordlist which comes preinstalled on Kali and is already installed on the machine. In order to crack it I ran the command pdfcrack -f flag.pdf -w /usr/share/wordlists/rockyou.txt, which revealed the password to be naughtylist.
Having found the password we could now open up the PDF file, which contained the flag THM{Cr4ck1ng_PDFs_1s_34$y}
Answer: THM{Cr4ck1ng_PDFs_1s_34$y}
What is the flag inside the encrypted zip file?
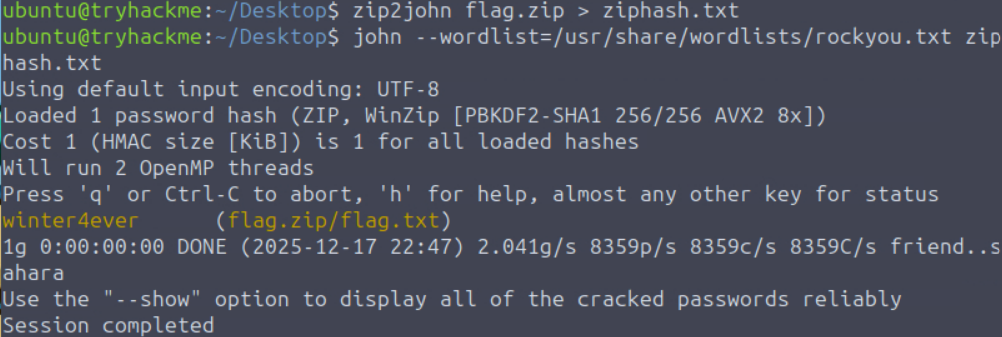
Next we needed to crack the zip file on the desktop named flag.zip. To do this we could use John the Ripper, but we first need to run the command zip2john flag.zip > ziphash.txt which extracts the password hash from the zip file into a text file that john can then crack. Just like before we can use the rockyou.txt wordlist to attempt to crack the hash using the command john --wordlist=/usr/share/wordlists/rockyou.txt ziphash.txt, which will attempt to crack the password by testing every word in the wordlist against the hash.
After letting it run for a little bit we find the password to be winter4ever, which we can then use to unlock the zip file.
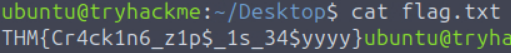
With the password in hand we just needed to unzip the archive using the command 7z x flag.zip and entering the password when prompted. We used 7z instead of the standard unzip command because the ZIP file uses an AES encryption method that the basic unzip tool doesn’t support. Once flag.txt was unzipped we simply read it using cat flag.txt, which shows the flag as being THM{Cr4ck1n6_z1p$_1s_34$yyyy}
Answer: THM{Cr4ck1n6_z1p$_1s_34$yyyy}
Have a look around the VM to get access to the key for Side Quest 2!
Although optional, side quests are a lot of fun, so I went ahead and looked for the key to unlocking the second side quest.
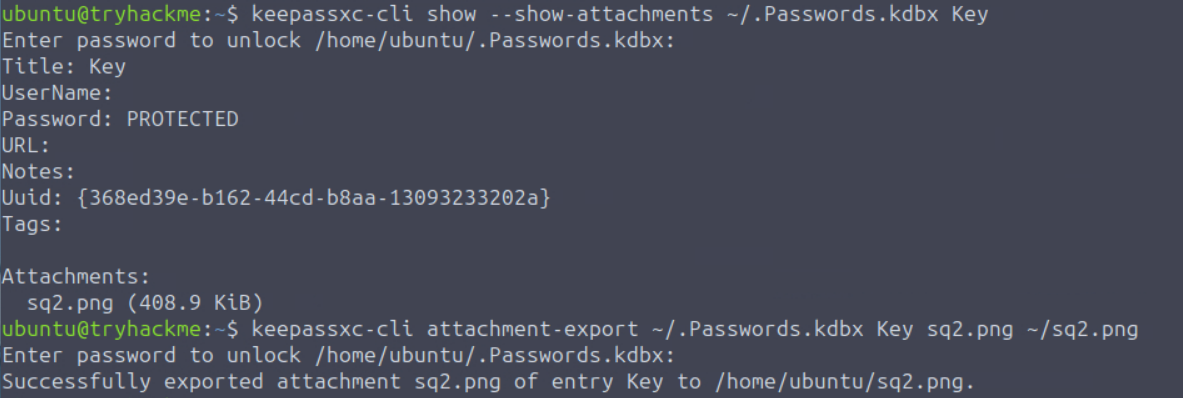
I began by searching for hidden files in the home directory, where I found .Passwords.kdbx, a KeePass database that could possibly be cracked if it had a weak master password. Just like with the zip file earlier we first needed to extract the database hash into a format that john could crack, which we can do using keepass2john ~/.Passwords.kdbx > keepass_hash.txt.
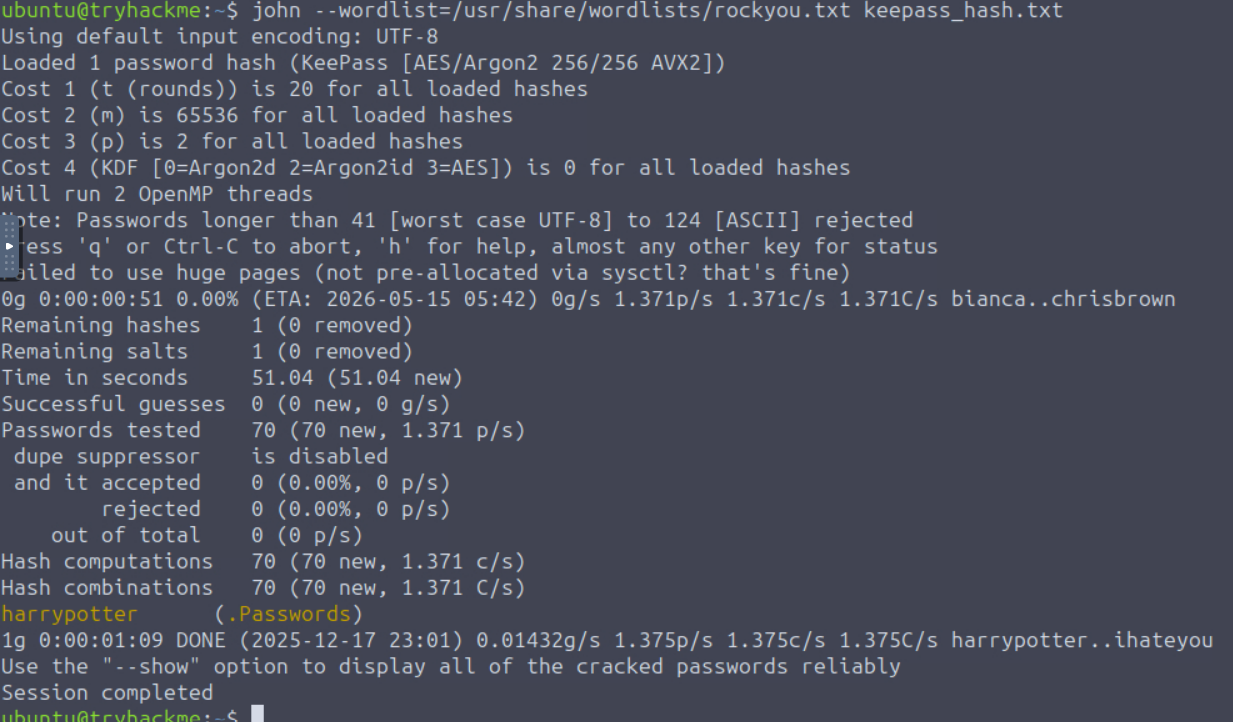
The keepass2john command wasn’t available in the standard PATH on THM’s machine, but it was available in the ~/Desktop/john/run/ directory. To specify it to run directly from that directory I ended up running the command ~/Desktop/john/run/keepass2john ~/.Passwords.kdbx > ~/keepass_hash.txt. Now that we had keepass_hash.txt we just had to run john --wordlist=/usr/share/wordlists/rockyou.txt keepass_hash.txt and wait to see if it finds something.
After letting it run for a while we found that the password is harrypotter, allowing us to access the KeePass database.
Now that we had the password we needed to access the KeePass file, but that requires a KeePass client to do. Using the which command I found keepassxc-cli to be installed on the THM machine. To see what entries were in the database I ran keepassxc-cli ls ~/.Passwords.kdbx and entered the password harrypotter when prompted. This showed a single entry called Key, which seemed promising for a side quest key.
To view the contents of this entry I ran keepassxc-cli show ~/.Passwords.kdbx Key, but the password field was marked as PROTECTED and didn’t display anything useful even when using the -s flag to show protected fields. After trying different flags, I realized the key might not be stored as a password field but as an attachment to the entry. Running keepassxc-cli show --show-attachments ~/.Passwords.kdbx Key confirmed this, revealing an attachment called sq2.png.
To extract the attachment I used keepassxc-cli attachment-export ~/.Passwords.kdbx Key sq2.png ~/sq2.png, which exported the png image to my home directory, which contained the key for side quest 2.
Key: tit_for_tat